Over 20,000 web servers (and who knows just how many websites) have already been compromised via trojanized WordPress themes to supply malware through malicious ads, Prevailion researchers discovered.
“This is probably due to the fact that many lack the required funding or human capital to create a completely custom website, unlike larger, more established firms,” the organization noted.
The strategy
The compromised servers are situated around the world and higher than a fifth of most compromised entities are small to mid-sized businesses.
The cybercriminals behind this scheme have already been at it since in latter part of 2017, plus they are not stopping.
They are taking benefit of the widespread usage of the WordPress content management system, a greater demand for premium themes and victims’ deficiency of security awareness to encourage them to unknowingly compromise their own web servers.
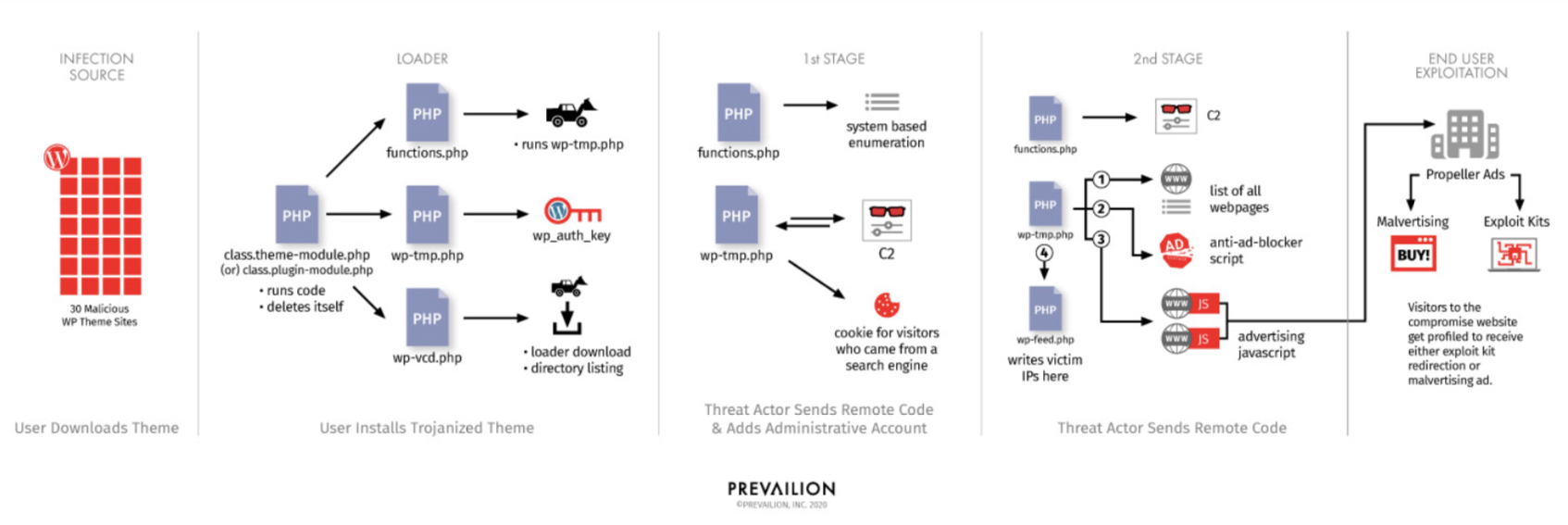
To achieve that, they’ve set up to 30 websites that ostensibly give thousands of totally free, pirated WordPress themes and plugins and hosted the trojanized themes and plugins in them – one of the most popular brands were Ultimate Support WooCommerce product filter, Slider Revolution and Chat.
Unmindful victims download and install the trojanized packages, which drop malicious files that permit the criminals to get full control over the web server. They are able to then add an administrative account, recover the web admin’s email account and WordPress password hash, and perhaps recover the password from it. (If the admin utilized the same password for additional accounts, it may also allow them to gain access to so some corporate resources.)
The delivered loader, first and second stage malware do things such as:
- Establish communications with the C&C server
- Download additional files from it
- Add a persistent cookie to website visitors who came to the site from one of several search engines and add their IP address to a list
- Collect information about the compromised machine
They also permit the criminals to include web links or keywords to existing or new webpages on the compromised domain (to boost the sites’ SEO profile), display ads on the visited webpage even if the end-user is using an ad-blocker, and deliver either genuine or malicious advertisements via the advertising service Propeller Ads.
“In several situations, the ads were completely benign and would direct the end user to a genuine service or website. In other cases nevertheless, we observed pop-up ads prompting the user to download potentially unwanted programs (PUP),” the researchers noted.
In other cases, the ad would redirect them to a domain hosting an exploit kit. If successful, the kit would drop a malware downloader onto the victim’s machine.
What can you do?
The researchers advise organizations to stop using pirated software, enable and update Windows Defender if their web server is running Windows, and never to reuse passwords across multiple accounts.
Customers should regularly update their OS and software program and consider utilizing a plugin like NoScript to avoid remote control JavaScript code from running on their machine.
The researchers named the malicious sites offering the trojanized themes and offered indicators of compromised that can help organizations check and detect whether their web servers have been compromised. Get more elaborate details from the researchers site.
Credit: Source






